Dot1x | Radius | AAA Complete Lab
OK this took some time to put together but its finally done, this is a full lab, setting up a DC with DHCP and DNS, a separate NPS that authenticates and authorizes users to connect to the LAN with 802.1x and also using RADIUS to authenticate logins to networking devices!
All from woe to go!
Step 1
Download and install the following;
-
GNS3 (current version)
-
Virtual box (current version)
-
Learn how to use them (youtube)
Step 2
-
Build, a couple of 2008 R2 boxes and a couple of Windows 7 64 bit boxes too for clients.
Step 3
-
Build the follwoing basic topology within GNS3

-
switches are IOU running IOS version 15.0
-
router is a 7200 running IOS version 15.0(1)M
-
The Domain controller and NPS/CA are Windows 2008 R2 Enterprise SP1
-
Win7- 2 is....Windows 7 64 bit
-
Address the network and get the base config done for connectivity,i used EIGRP for simplicity.
Step 4.
Build the DC
1. Set an admin password,i used "Password123" classic!
-
Close the auto opening "server manager" and "quick start" page, check the boxes to make sure they don't come back, they're not the boss of me!
2. Server Manager==>Roles==>Add Roles==>Skip this page by default==>Next==>Check "Active Directory Domain Services"==>Add required .NET 3.5.1 features==>Next==>Next==>Install
Done!

-
3.Assign a static iP to the DC
First change the Virtualbox network adaptor to "Generic Driver"

-
Then change the IP of the adaptor;

-
4. Promote the DC!

-
Next==>Next==>Create a new domain in a new forest==>Next==>Mycertstudies.local==>Next==>Windows 2008 R2==>Next==>DNS Server==>Next==>Yes==>Next==>Password123/Password123==>Next==>Next==>Reboot on completion
5. Build some sort of custom AD OU's and stuff for your computers and user accounts...(you can tell a network guy did this!)
I also created a copy of the admin account for myself and put it in the "IS" OU and i created a blank user "rjunk" and put him in the "ER" OU.

-
Done!
Step 5
Build the NPS/CA!
First off, assign the box an IP, i used 10.2.0.200 and point it to the DC for DNS
Then Join it to your domain!





-
Server Manager==>Roles==>Add Roles==>Next==>Check the following;

-
Next==>Next==>Check the following services;

-
Next==>Select Create a self-signed Certificate;

-
Next==>Next==>Certificate Authority==>Next==>Enterprise==>Next==>Root CA==>Next==>Create a new private key==>Next x 6==>Install

-
Done!
-
Step 6
Request a cert for the NPS from the CA
Start Menu==>Run==>mmc.exe==>File==>Add/remove Snap-ins;
Certificates==>Add==>Computer account==>Local Computer==>Finish==>OK

-
Expand Certificates==>Personal==>Right click on Certificates==>All Tasks==>Request New Certificate;

-
Next==>Next==>Computer==>Enroll==>Finish


-
Done!
Configure NPS for radius logins
-
Add radius client for the switch that will be sending the request....
-
Server Manager==>Roles==>NPS==>Radius Clients and Servers==>Right click "Radius Clients"==>New

-
Add Connection Request Policy
Server Manager==>Roles==>NPS==>Policies==>Right click "Connection Request Policies"==>New
Copy the following Policy called "Connection"

-
Add the Network Policy
Server Manager==>Roles==>NPS==>Policies==>Right click "Network Policies"==>New
Copy the following Network Policy called "Policy"
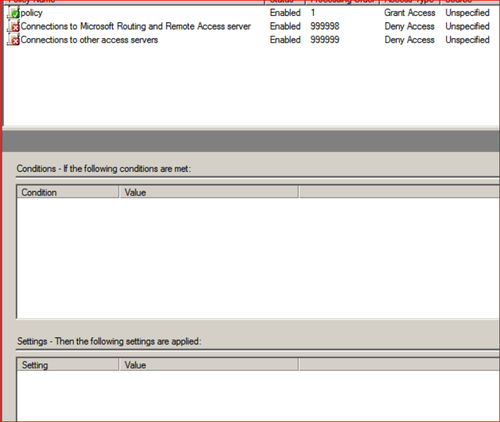
This gives you a very generic policy that will allow users to login, you can add restrictions, conditions and other parameters from here...now;
Configure the radius client (the switch)
no ip routing
ip
default-gateway 10.1.0.1int
vlan 1
ip add 10.1.0.50 255.255.255.0
!
username cisco secret cisco
enable secret cisco
!
aaa new-model
aaa authentication login default local group radius
radius-server host 10.2.0.100 key Password123
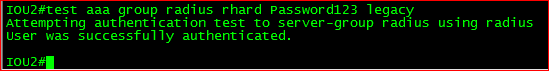
Test a login!
From user exec;
test aaa group radius rhard Password123 legacy




