New or re-issue of an SSL Certificate
There are different processes depending on what you are trying to achive, is it a new cert you are purchasing? is it a renewal of an existing one? or are you simply reissuing the existing valid certificate?
If you are requesting a new cert follow the process below, if you are renewing a cert, follow the process below, if you are re-issuing an existing valid certificate, simply go to the vendor, download the bundle and apply.
Generate the CSR
The first step is to generate the Certificate Signing Request or CSR, some systems do this in different ways, i.e from the command line or a custom application, but the important thing is to remember and take note of where you generated the CSR, this will be needed later (private key)
To ensure a consistent approach i always use our local CA to generate all CSR's if the system concerned allows it.
In this example, i'll use Windows Internet Information Services Manager (IIS)
RDP to your CA and from Server manager, click 'Tools' and then 'Internet Information Services Manager ' then double click on Server certificates (on the right)

On the right, click "Create Certificate Signing Request"

Then fill out the required information, note that if you are requesting a wildcard, the "*.yourdomain.com" would go in the "Common Name" field.

Then select the default Cryptographic provider, change to 2048 bit and hit Next;

Now navigate to your CSR storage folder on the local device and choose a name that you will remember, its a good idea to suffix it with_CSR - then click "Finish"

Navigate to the CSR Storage folder, open the CSR in a text editor, copy the text contents of the file;

Submit your CSR
Go back to the vendors website and follow the process to reissue or request the certificate, this will vary with vendor and type of certificate, but you will have to paste in the CSR into a prompt and then validate the certificate request via email or other method.
With “namecheap” they will email a validation code, within the same email will be a string, follow the link and paste in the string, you will then be able to download the certificate pack (this could just contain 1 certificate).
Copy the certificate pack to your CA Certificate Store! - this is essential to keep everything centralized.
Download the certificate pack to your desktop and extract if necessary, the folder should contain the following (or only 1);

Complete the CSR Request
Go back to your CA and click on “Complete Certificate Request” in IIS Manager on the right hand side.
Select the location of the .crt certificate that was downloaded, give it a friendly name which should be the url of the website
separated by underscores (unlike below) and click OK;
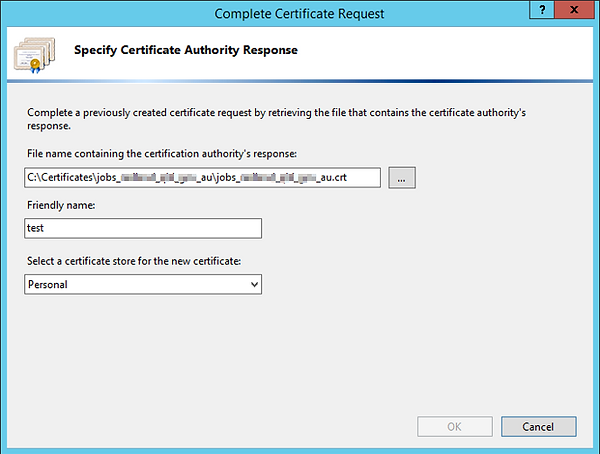
During this process you will be asked for a password, this password MUST be stored in a secure location, like a password manager application.
In the end it will produce a .pfx or PKCS12 file
Copy this certificate to your CA as a record!!
What has just happened is that the server will look at the certificate from the vendor, look at the private key, and do some black magic, this results in the production of the .pfx certificate, which is essentially the cert and the key in one, but it is protected with the password so don't forget it!
Import New Certificate
Go back to the webserver, (mmc.exe certificate addin) and import the certificate into the personal store

Select the .pfx Certificate and click Next;
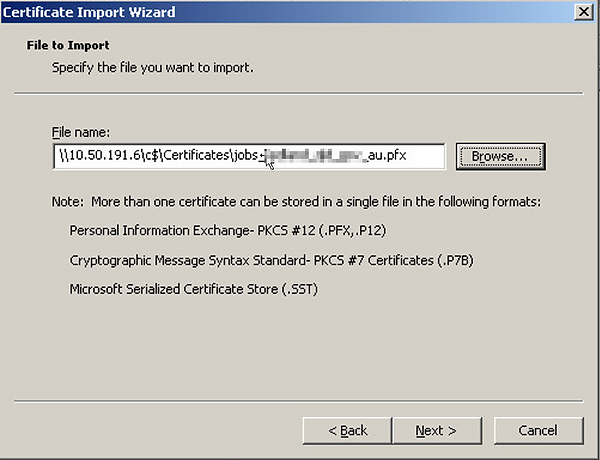
Once its imported into the store, double click on it to confirm its validity, confirm the validity of the full certification path;

Apply the New Certificate
Go back to IIS manager and right click on “Default web site” select “Properties”

Click “Directory Security” tab and under “Secure Communications” click “Server Certificate”
Click “Next” then select “Replace the current certificate”

Click next, select the new certificate and follow the bouncing ball until complete.
Now test the website! (ctrl-f5 maybe necessary)
Verify the Path
You need to confirm that there are no issues at all across all major platforms, an absolutely amazing site for this is
SSL Labs - go there and confirm that you have no certificate issues - the report will take around 1 minute, be patient
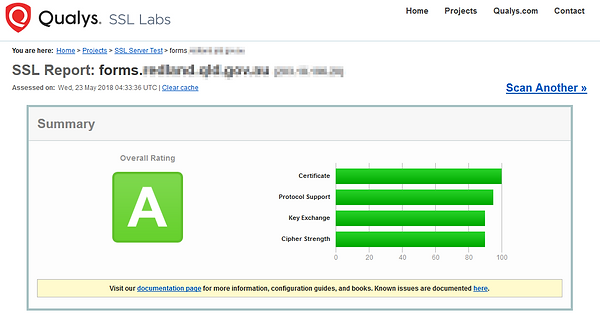
Now just cause you got an A, doesn't mean your good to go, expand the "Certification Path" field at the bottom of the first section and scroll through the tabs to confirm that all will be good on all platforms; not below Path#1 is trusted for Mozilla, but path#2 is not complete, this was the same for android;

Now what you have to do is copy the fingerprint of the required intermediate certificate and google it, no really, google it;

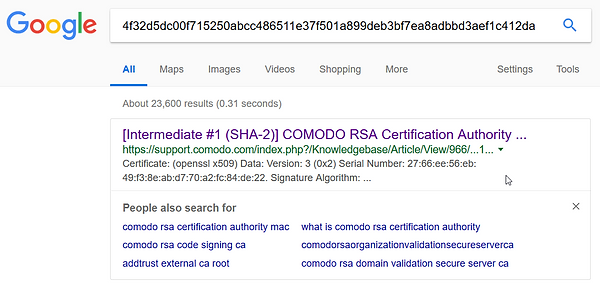
Goto the link and download the certificate - you will end up with a .crt file;

Now go to your IIS box (or firewall in this case) and upload the intermediate certificate, on a windows box, copy it to the box and simply double click, install.

Now confirm that is actually installed on the box;

Now run the test again on https://www.ssllabs.com/ssltest:

Clean up
Go back to the webserver (or other device) and delete the old certificate from the personal store.



